ATM thefts have gone high-tech, and judging by how the police and banks are running around like a headless chicken trying to piece together the puzzle, the local authorities and financial institutions were obviously not ready for such an attack. And it’s not hard to understand why – the police and banking institutions were trapped in stone age mentality where they thought the bad guys will always be the same “Oxy Gang”, using oxy-acetylene blow torch to open the machine’s cash compartment.
That was so yesterday. To make things worse, banking institutions blinded by greediness had resorted to squeeze every penny of profits by cutting off security guards manning ATM machines. They depend on merely CCTV cameras and alarm systems as their only defence. Hence, the latest ATM thefts methodology has left the authorities head scratching. So far, 14 bank branches belonging to Affin Bank, Al Rajhi Bank and Bank Islam were reportedly hacked into by a Latin American gang which made off with over RM3 million.
Malaysian Bukit Aman Commercial Crime Investigation Department chief Comm Mortadza Nazarene revealed that the suspects used a computer malware known as “ulssm.exe” to hack into the ATMs. The suspects were found to have opened the top panel of the machine without using a key and inserted a compact disc into the machine’s processing centre which caused the ATM’s system to reboot.
The sophisticated gang then used a keyboard to hack into the system and take out money. According to systems engineer of a bank – up to 40 notes could be taken out in a single transaction using the method. Needless to say, the absence of security guard ease the gang’s task, so much so that they could go for a spa or coffee session before coming back to collect their loots.
But is this something very new as if it was invented yesterday? Actually, the risk of using such malware or to be precise – ATM trojan horse – was published back in May 2014. What this means is, somebody had already done that using the same method somewhere in the world. Unfortunately, the police were too busy carrying orders from their politician masters arresting opposition for petty and silly seditious allegations.
As far back as 2010, computer security experts have shown how ATM machines can be hacked to spit money, using hardware kit that cost less than US$100 to make. And the ATM’s motherboard is only protected by a door, of which you can buy the “universal key” online (*grin*). You can then used a USB port on the motherboard to upload your own software (stored in your USB stick), which changed the device’s display, played a tune, and made the machine spit out money.
So, how did the high-tech Latin American gang hacked and stole RM3 million (US$920,000; £560,000) in a couple of nights? It all started with Microsoft – they stopped supporting Windows XP operating system after 8th April, 2014. In other words, even if the ATM trojan horse was discovered one day after the end-of-support date, Microsoft will not release any security patches to plug the threat, period.
The problem is there are up to 95% ATM machines still running on Windows XP. Again, due to cost and profit, banking institutions prefer to close one-eye and pretend as if their ATMs were as secured as the Alcatraz. In the case of Malaysian ATM thefts, the Latin Americans could most likely infected their compact disc with “Backdoor.Padpin” trojan horse. Once the CD is inserted, the ATM reboots and execute the trojan horse, which create the following file:
- [PATH TO THREAT]\ulssm.exe
The Trojan then creates the following registry entries so that it runs every time Windows starts:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\”ulssm.exe” = “[PATH TO THREAT]\ulssm.exe“
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\”ulssm.exe” = “[PATH TO THREAT]\ulssm.exe“
The Trojan can delete itself if it fails to gain control of the PIN pad or dispenser. It runs in the background until a specific code is entered on the ATM’s PIN pad. Finally, it then opens a back door on the ATM running Windows XP, allowing an attacker to perform the following actions:
- Display cassette information such as bills left, denomination and total amount per cassette
- Dispense money from the compromised ATM
- Select which cassette the ATM dispenses money from
- Temporarily disable the local network to avoid triggering alarms when withdrawing money
- Extend the duration of the session in order to continue stealing money
- Delete the Trojan from the compromised ATM
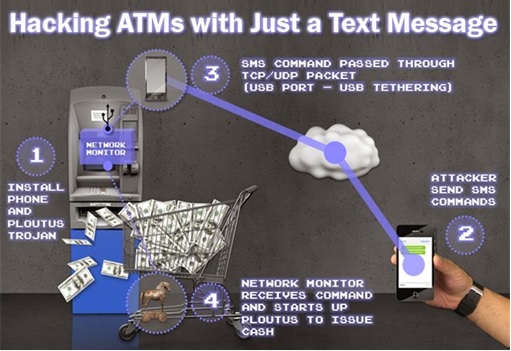
There’s also another famous trojan horse – Backdoor.Ploutus – which was discovered in 2013 to hack ATMs in Mexico. Amazingly, this Ploutus trojan allows cybercriminals to simply send an SMS to the compromised ATM, then walk up and collect the dispensed cash. Here’s how it works:
- Connect a mobile phone to the machine with a USB cable and install Ploutus Trojan.
- Sends two SMS messages to the mobile phone inside the ATM.
- SMS 1 contains a valid activation ID to activate the trojan horse
- SMS 2 contains a valid dispense command to get the money out
- Mobile attached inside the ATM detects valid incoming SMS messages and forwards them to the ATM as a TCP or UDP packet.
- Network packet monitor (NPM) module coded in the trojan receives the TCP/UDP packet and if it contains a valid command, it will execute Ploutus
- Amount for Cash withdrawal is pre-configured inside the trojan horse itself.
- And voila, the hacker can collect cash from the hacked ATM machine.
At the moment, it’s not sure if the Latin American gang used the “Padpin” or “Ploutus” trojan, or another type of variant. If police’ revelation is true, and not just another marketing stunt to convince the public about their efficiency, then the first method could be used. But that does not explain the phone SIM card usage during the ATM hacking operation, as what the police have claim.
Whichever the method used, the Latin American gang did one huge mistake – they forgot to erase their foot trail by deleting their trojan from the ATMs hacked and robbed. Perhaps they were too excited and surprised with the lack of banking security in this country. Either way, the fact that no security guard was deployed to this “goldmines” can only means one thing – the hacking spree is going to continue (*tongue-in-cheek*).
Other Articles That May Interest You …
- Biggest Celebrity Hacking Scandal – Nude Photos Of Jennifer Lawrence, Kate Upton & 100 Other Celebrities
- Here’s How Xiaomi Secretly Steal Your Data For Chinese Govt, And How You Can Block It
- Exposed !! Documents Show Malaysian Foreign Minister Lies About Diplomat Rape Scandal
- Beware! Here’s How Government’s Spying On You, Legally
- Credit Card Safety Tips That You May Have Missed
- Despite Being Hacked, Malaysian Govt Shows Arrogance
- Anonymous Hackers, Don’t Say I Didn’t Warn You
- Watch Out China, 25% Of U.S. Hackers Are FBI Informer

|
|
September 30th, 2014 by financetwitter
|

|

|

|

|

|

|
Comments
Actually, if the information presented in this article is correct the incompetence of the financial institutions IT team is beyond comprehension. What work PC in function today would still have autorun enabled for CD drives or USB ports?
I think the customers of said banks are better off keeping their money under their mattresses.
really haramjada? there’re tons of other things you could use to make the card slot unusable dude … why the trouble of using sim card? i can pick up any rubbish on the street to do the task … go figure …
So many grammar mistakes in this article. Plural is used where it should be singular etc…
On the security guards with ATMs. I don’t know any countries where this is done and this would be too costly. They just need to improve security in other ways. Perhaps by putting ATMs behind a secured doors which require users to swipe their debit cards to open the door (as they can trace that) and more robust hardware and software security measures that trip alarms when someone tries to tamper with the ATM.
Onus is with the people (the banks) to prevent the crime and the fault if this is the unscrupulous thieves, not the police.
It is like if i leave my house door wide open and I got robbed there after. The fault is with me not the police. The job of the police is to help me, in this case, for my stupidity.
yeah arro … and the grammar will only get worse, so stay tune …
let’s see:
if system=sucks; then
patch it;
else
guards=yes;
else
risk=high;
endif
your suggestions are good … still, it will incur extra cost to the banks … and the total cost of ownership could be more than getting a physical guard …
cheers …
good opinion citizen malaysia,
it works both way, will your house get robbed even when it’s not locked? well, it depends, ask your parents whether they need to lock their house / gate during their teenage time …
why the country was so secured last time that you don’t have to lock your house and car but still your belongings would still stay intact, but not now?
of course in this case, we can conveniently blame it on technology … the question: is police’s cyber-crime unit well-equipped and knowledgeable to tackle such problem, which can only get worse?
cheers …
It’s fine for you, the author, to theorize and be imaginative about the incident. But to tie it to politics only goes to show what a narrow-minded moron you are.
okay einstein mike, please enlighten us one institution that has not been tainted with politics here?
FinanceTwitter Agreed. Last time was much more safer.
Why was last time more safer? Was it because the police were better? or the people were better?
So now if it is not safe is it because the police was lousier then last time? or is it because people are becoming worse compared to last time?
The police can only act once the crime is committed thereby arresting the perpetrator thus removing him (curing) from society. But the problem is deeper then that. It lies in the very fabric of our society to prevent it from happening again by another perpetrator. As we all know prevention is better then cure.
So let us do what we can to stop the rot in our society. And help the police, remove the bad apples from our society like what majority of your article is doing by raising awareness.
They failed the basic access control. Who else is to blame other than the bank themselves. Saving cost by cutting few hundred security guards and end up losing millions.




































your dumb. the sim card was used to hold the card slot so that shile they wait at coffee shop, nobody can use the machine.